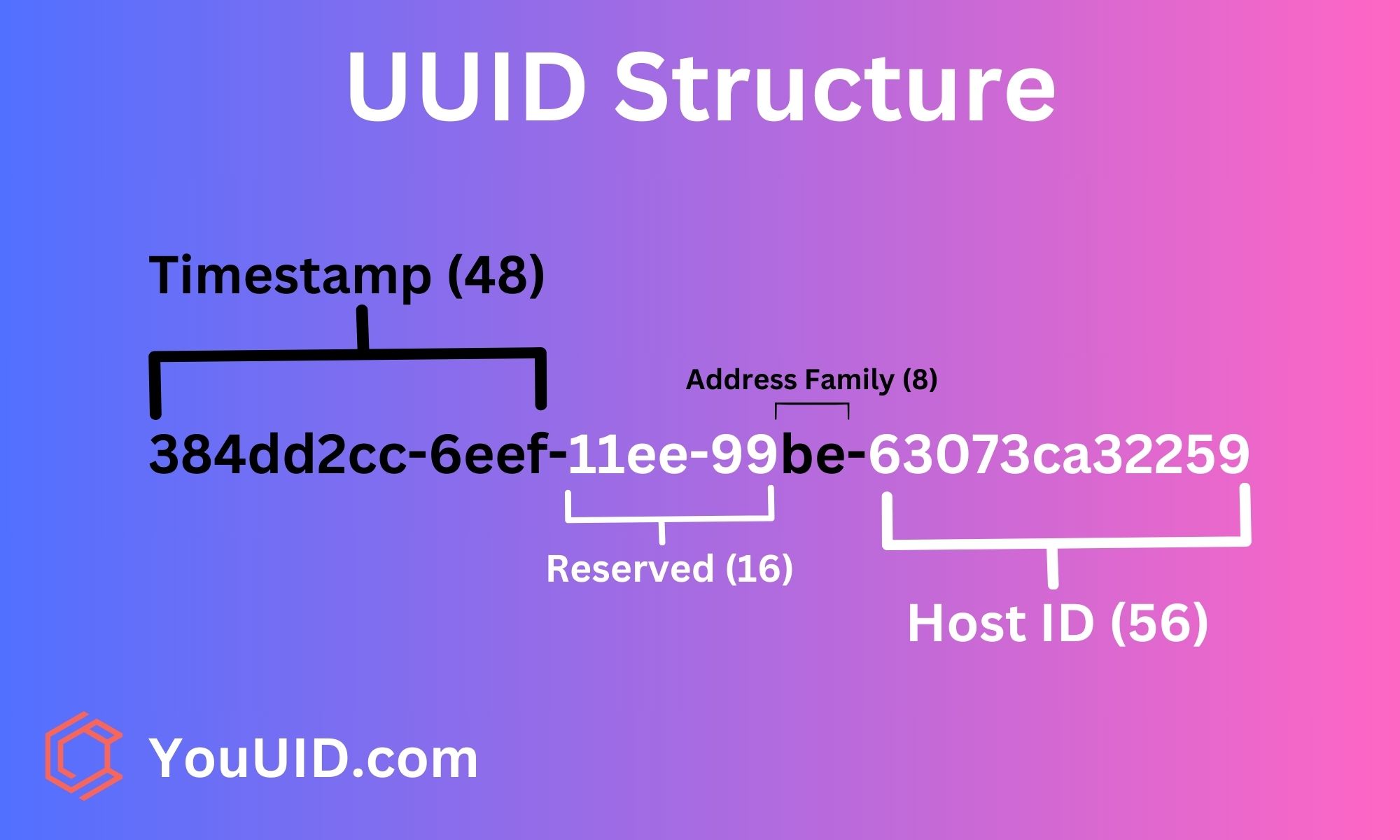
What is a UUID?
A UUID, or Universally Unique Identifier, is a 128-bit value used to uniquely identify information in computer systems. The term Globally Unique Identifier (GUID) is also used, mostly in Microsoft systems.
UUIDs are often used as primary keys in database tables, to identify files and other resources on a computer, or to track users and devices across multiple systems. They can also be used to create pseudonyms or aliases that can be used to protect privacy.
UUIDs are generated using a variety of algorithms, but they are all designed to be extremely unlikely to collide. This means that the chances of two different systems generating the same UUID are very low, even if they are using the same algorithm.

Uses of UUIDs
UUIDs are used in a variety of ways, including:
- Database primary keys: UUIDs can be used as primary keys in database tables to ensure that each row in the table has a unique identifier. This makes it easy to quickly and efficiently query and update the data in the table
- File identifiers: UUIDs can be used to identify files and other resources on a computer. This makes it easy to track down files and to ensure that they are not overwritten or deleted accidentally. For example, many cloud storage providers use UUIDs to identify files stored in the cloud
- User and device tracking: UUIDs can be used to track users and devices across multiple systems. This is useful for applications such as single sign-on and analytics. For example, many websites use UUIDs to track users who are logged in to their site
- Privacy protection: UUIDs can be used to create pseudonyms or aliases that can be used to protect privacy. For example, a user could use their YouUID to create a pseudonym for use in online forums. This helps to keep their identity safe and private
How UUIDs are generated?
There are a variety of algorithms that can be used to generate UUIDs. The most common algorithm is version 4 UUIDs, which are generated using a pseudo-random number generator. Version 4 UUIDs are guaranteed to be unique with a probability of 1 - 10^-36.
Other types of UUIDs include:
- Version 1 UUIDs, which are generated using a timestamp and a MAC address. This makes them useful for tracking devices or users across multiple systems
- Version 3 and 5 UUIDs, which are generated using a hash function. This makes them useful for creating unique identifiers based on other data, such as a user's email address or a file's checksum

Security of UUIDs
UUIDs are generally considered to be very secure. However, there are some potential security risks associated with using UUIDs.
One potential security risk is that UUIDs can be used to track users across multiple systems. If a user's UUID is leaked, it could be used to track the user's activity across all of the systems that they use.
Another potential security risk is that UUIDs can be used to generate predictable values. For example, if an attacker knows the timestamp and MAC address of a system, they could generate a predictable UUID for that system.
To mitigate these security risks, it is important to use strong algorithms to generate UUIDs and to keep UUIDs secret. It is also important to use UUIDs in conjunction with other security measures, such as encryption and authentication.
Why UUIDs are important in development?
UUIDs are important in development because they provide a unique and permanent way to identify information in computer systems. This makes them ideal for use as primary keys in database tables, to identify files and other resources on a computer, or to track users and devices across multiple systems.
UUIDs are also important in development because they can be used to protect privacy. By using UUIDs to create pseudonyms or aliases, developers can help to keep their users' identities safe and private.
Benefits of using UUIDs in development
There are several benefits to using UUIDs in development, including:
- Uniqueness: UUIDs are extremely unlikely to collide, even if they are generated by different systems using different algorithms. This makes them ideal for use as unique identifiers
- Immutability: UUIDs are permanent and cannot be changed. This makes them ideal for use as primary keys in database tables or to identify files and other resources on a computer
- Privacy: UUIDs can be used to create pseudonyms or aliases that can be used to protect privacy. For example, a developer could use UUIDs to create pseudonyms for users in their application
- Portability: UUIDs are universally unique, which means that they can be used to identify information across different systems. This makes it easy to port applications and data between different systems
How to use UUIDs in development?
UUIDs can be used in a variety of ways
Here are some examples of how UUIDs can be used in development:
- Database primary keys: UUIDs can be used as primary keys in database tables to ensure that each row in the table has a unique identifier. This makes it easy to quickly and efficiently query and update the data in the table. For example, the following SQL statement creates a table with a UUID primary key:
- File identifiers: UUIDs can be used to identify files and other resources on a computer. This makes it easy to track down files and to ensure that they are not overwritten or deleted accidentally. For example, the following Python code generates a UUID and uses it to create a new file:
- User and device tracking: UUIDs can be used to track users and devices across multiple systems. This is useful for applications such as single sign-on and analytics. For example, the following Java code generates a UUID and stores it in a cookie:
- Privacy protection: UUIDs can be used to create pseudonyms or aliases that can be used to protect privacy. For example, a developer could use UUIDs to create pseudonyms for users in their application. This helps to keep their users' identities safe and private. For example, the following PHP code generates a UUID and uses it to create a pseudonym for a user:
CREATE TABLE users (
id UUID NOT NULL PRIMARY KEY,
name VARCHAR(255) NOT NULL,
email VARCHAR(255) NOT NULL UNIQUE
);
import uuid
# Generate a UUID
uuid = uuid.uuid4()
# Create a new file with the UUID as the filename
with open(str(uuid), "w") as f:
f.write("This is a new file")
import java.util.UUID;
// Generate a UUID
UUID uuid = UUID.randomUUID();
// Create a cookie with the UUID as the value
Cookie cookie = new Cookie("uuid", uuid.toString());
// Set the cookie expiration date to one year
cookie.setMaxAge(365 * 24 * 60 * 60);
// Add the cookie to the response
response.addCookie(cookie);
Conclusion
UUIDs are a versatile and powerful tool that can be used to uniquely identify information in computer systems. They are often used as primary keys in database tables, to identify files and other resources on a computer, or to track users and devices across multiple systems. UUIDs can also be used to create pseudonyms or aliases that can be used to protect privacy.
UUIDs are an important tool for developers to know about and to use in their applications. By using UUIDs, developers can create more secure, portable, and privacy-friendly applications.
